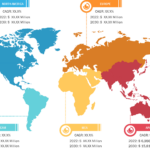
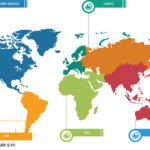
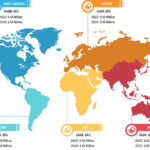
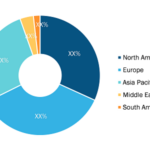
Increasing Number of Connected Devices Drives Public Key Infrastructure Market Growth Public key infrastructure is also known as asymmetric cryptography, and it uses two pairs of keys—one is public and the other private. A key is generally a long binary number, while a root key is the topmost key in the public key infrastructure hierarchy. […]
Headline
Tag: Public Key Infrastructure Industry
Back To Top